Hello folks!
Link to Part 2: SCCM – Enabling ‘Easy’ Local Login on Domain Computers During OSD Part 2 of 2: Applying The Info
In my organization we have need for the occasional machine to be configured with local login for such things as display computers or book sign-out machines in a library. Local login is easy, but having to revisit the machine after imaging to set it up is annoying and, frankly, a waste of time. Unfortunately we hadn’t been successful or too interested in solving this. Until now that is.
WARNING: This will be highly specific (yet generalized) to our implementation. It is my hope that somehow you find some use out of this.
Part 1 will cover getting the info at the start of your task sequence while Part 2 will cover the application of the info to the machine.
Credit where credit is due: https://www.scconfigmgr.com/2014/06/06/prompt-for-ou-location-during-osd-with-powershell/ was where the start of this all came from.
Here we go…
The code (Get-LocalUserInfo.ps1)…
param(
[parameter(Mandatory=$true)]
[string]$RBOptionFirst,
[parameter(Mandatory=$true)]
[string]$RBOptionSecond,
[parameter(Mandatory=$true)]
[string]$RBOptionThird
)
function Load-Form {
$LocationList = @("A location", "Another location", "One more")
$Form.Controls.AddRange(@($RBOption1, $RBOption2, $RBOption3, $ComboBox, $Button, $GBSystem, $GBLocation))
$ComboBox.Items.AddRange($LocationList)
$Form.Add_Shown({$Form.Activate()})
[void]$Form.ShowDialog()
}
function Set-UserLocation {
param(
[parameter(Mandatory=$true)]
$Location
)
if ($RBOption1.Checked -eq $true) {
$UserName = "$($RBOptionFirst)"
}
if ($RBOption2.Checked -eq $true) {
$UserName = "$($RBOptionSecond)"
}
if ($RBOption3.Checked -eq $true) {
$UserName = "$($RBOptionThird)"
}
$TSEnvironment = New-Object -COMObject Microsoft.SMS.TSEnvironment
$TSEnvironment.Value("LocalUserName") = "$($UserName)"
$TSEnvironment2 = New-Object -COMObject Microsoft.SMS.TSEnvironment
$TSEnvironment2.Value("LocalUserLocation") = "$($Location)"
$Form.Close()
}
# Assemblies
[void][System.Reflection.Assembly]::LoadWithPartialName("System.Drawing")
[void][System.Reflection.Assembly]::LoadWithPartialName("System.Windows.Forms")
# Form
$Form = New-Object System.Windows.Forms.Form
$Form.Size = New-Object System.Drawing.Size(260,220)
$Form.MinimumSize = New-Object System.Drawing.Size(360,220)
$Form.MaximumSize = New-Object System.Drawing.Size(360,220)
$Form.SizeGripStyle = "Hide"
$Form.StartPosition = "CenterScreen"
$Form.Icon = [System.Drawing.Icon]::ExtractAssociatedIcon($PSHome + "\powershell.exe")
$Form.Text = "Choose user details"
$Form.ControlBox = $false
$Form.TopMost = $true
# Group boxes
$GBSystem = New-Object System.Windows.Forms.GroupBox
$GBSystem.Location = New-Object System.Drawing.Size(10,10)
$GBSystem.Size = New-Object System.Drawing.Size(320,60)
$GBSystem.Text = "Select user"
$GBLocation = New-Object System.Windows.Forms.GroupBox
$GBLocation.Location = New-Object System.Drawing.Size(10,80)
$GBLocation.Size = New-Object System.Drawing.Size(220,60)
$GBLocation.Text = "Select location"
# Radio buttons
$RBOption1 = New-Object System.Windows.Forms.RadioButton
$RBOption1.Location = New-Object System.Drawing.Size(20,33)
$RBOption1.Size = New-Object System.Drawing.Size(100,20)
$RBOption1.Text = "$($RBOptionFirst)"
$RBOption1.Add_MouseClick({$ComboBox.Enabled = $true})
$RBOption2 = New-Object System.Windows.Forms.RadioButton
$RBOption2.Location = New-Object System.Drawing.Size(120,33)
$RBOption2.Size = New-Object System.Drawing.Size(100,20)
$RBOption2.Text = "$($RBOptionSecond)"
$RBOption2.Add_MouseClick({$ComboBox.Enabled = $true})
$RBOption3 = New-Object System.Windows.Forms.RadioButton
$RBOption3.Location = New-Object System.Drawing.Size(220,33)
$RBOption3.Size = New-Object System.Drawing.Size(100,20)
$RBOption3.Text = "$($RBOptionThird)"
$RBOption3.Add_MouseClick({$ComboBox.Enabled = $true})
# Combo Boxes
$ComboBox = New-Object System.Windows.Forms.ComboBox
$ComboBox.Location = New-Object System.Drawing.Size(20,105)
$ComboBox.Size = New-Object System.Drawing.Size(200,30)
$ComboBox.DropDownStyle = "DropDownList"
$ComboBox.Add_SelectedValueChanged({$Button.Enabled = $true})
$ComboBox.Enabled = $false
# Buttons
$Button = New-Object System.Windows.Forms.Button
$Button.Location = New-Object System.Drawing.Size(140,145)
$Button.Size = New-Object System.Drawing.Size(80,25)
$Button.Text = "OK"
$Button.Enabled = $false
$Button.Add_Click({Set-UserLocation -Location $ComboBox.SelectedItem.ToString()})
# Load Form
Load-Form
As the above link mentions, using this script requires that Microsoft .NET (WinPE-NetFx) and Windows PowerShell (WinPE-PowerShell) be added to your boot wim and (re)ristributed to your distribution points.
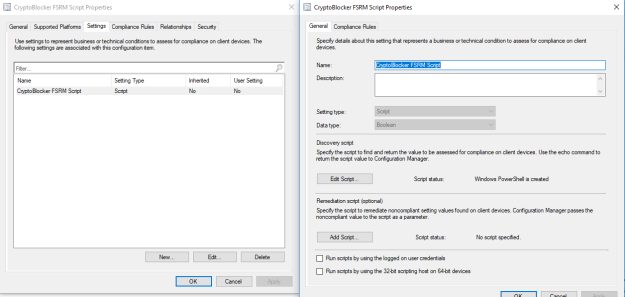
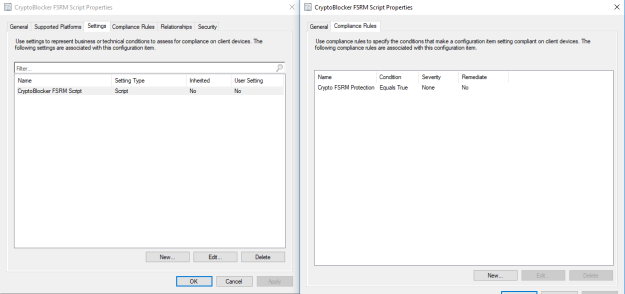
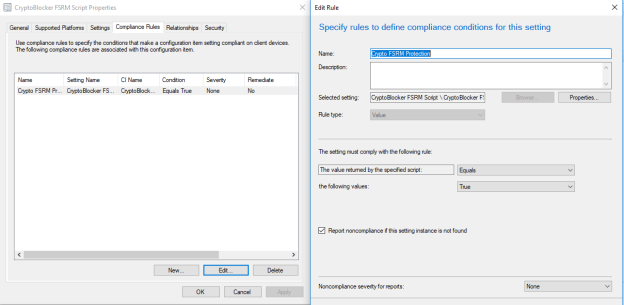
Save the above script to your package source location and create a package for it. In my case, the name is ‘Set Local user Info’ and includes some other scripts and components which will be discussed in Part 2.
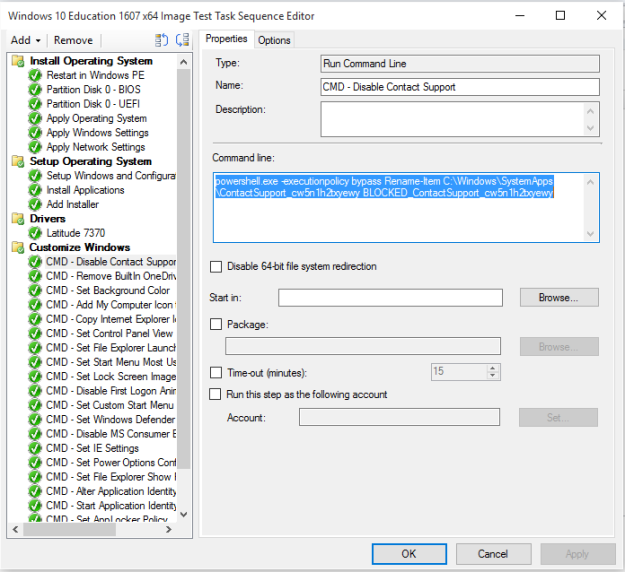
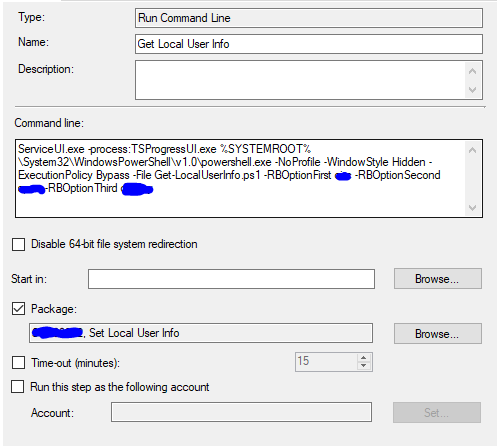
Create a “Run Command Line” task sequence step early in the TS list:

And configure it as follows:
If all goes well, the following will appear when you begin your task sequence…
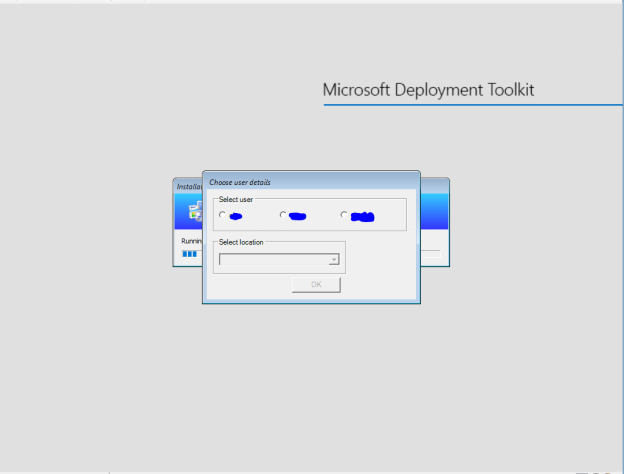
Selecting either of the three radio buttons allows the location drop down list to appear. Select the name/type of user you passed via the command line and then pick the location (why this is offered is covered in Part 2).
Stay tuned for Part 2!